In the initial years of the 2020s, quantum computing emerged in the public arena as a possible menace to Bitcoin. Based on the SHA-256 cryptographic hash function for its proof-of-work consensus mechanism, Bitcoin’s worth depends on computational strength.
If a technology emerges that can bypass the conventional binary system of 0s and 1s for data units, it could potentially revolutionize cryptography as we recognize it. But is that threat overstated?
Could quantum computing at some point render Bitcoin a worthless snippet of code? Let’s begin by grasping why Bitcoin depends on cryptography.
Bitcoin’s Bits and Hashing
When we indicate that an image occupies 1 MB of space, this signifies it comprises 1,000,000 Bytes. Since each Byte contains 8 bits, an image holds 8,388,608 bits. Bits, the binary digit, represent the smallest unit of information, either 0 or 1, that forms the entire structure of our digital era.
For an image, the bits in a 1MB file would allocate a color to each pixel, facilitating human readability. In the context of a cryptographic function like SHA-256 (Secure Hash Algorithm 256-bit), developed by the NSA, it generates 256 bits (32 Bytes) as a fixed-length hash derived from an input of any size.
The central function of a hash algorithm is to transform any string of letters or numbers into an output of consistent length. This blending of obfuscation makes it suitable for compact storage and anonymized signatures. Furthermore, since the hashing procedure is unidirectional, the hashed data becomes effectively irreversible.
Therefore, when we state that SHA-256 offers 256-bit security, we imply that there are 2256 potential hashes to contemplate for reversal. When Bitcoin transactions occur, each Bitcoin block features its own distinct transaction hash generated by SHA-256. Each transaction within the block contributes to this unique hash as they form the Merkle root, along with the timestamp, nonce value, and other metadata.
An aspiring blockchain attacker would need to recalculate hashes and extract the required data not just for the block containing the transactions but for all following blocks linked to it. Suffice it to say, the 2256 possibility load presents an almost unfeasible computational challenge, necessitating a tremendous investment of energy and time, both of which are extremely expensive.
But could this still be the case with quantum computing?
New Quantum Paradigm for Computing
Departing from bits as mere 0s and 1s, quantum computing introduces qubits. Utilizing the characteristic of superposition, these information units can represent both 0 and 1 simultaneously. In other words, we shift from deterministic computing to indeterministic computing.
As qubits can inhabit an entangled and superimposed state until observed, computations become probabilistic. Moreover, since there are more states than solely 0 or 1, a quantum computer possesses the capacity for parallel computing as it can process 2n states concurrently.
A traditional binary computer would have to execute a function for each potential 2n state, which the quantum computer could evaluate at once. In 1994, mathematician Peter Shor conceived an algorithm with this concept in mind.
Shor’s algorithm integrates Quantum Fourier Transform (QFT) and Quantum Phase Estimation (QPE) methodologies to enhance pattern-finding and theoretically defeat all cryptographic systems, not just Bitcoin.
Nonetheless, there exists a significant issue. If quantum computing is probabilistic, how dependable is it?
Stabilizing Coherence in Quantum Computing
When it is claimed that qubits are superimposed, it is analogous to picturing a coin flip. While airborne, one can envision the coin exhibiting both states – heads or tails. However, once it lands, the state resolves into a single outcome.
Similarly, when qubits are resolved, their state collapses into the classical state. The challenge is that a revolutionary algorithm like Shor’s necessitates many qubits to sustain their superposition for an extended duration to interact effectively. Otherwise, the vital calculations fail to be completed.
In quantum computing, this phenomenon refers to quantum decoherence (QD) and quantum error correction (QEC). Additionally, these challenges must be addressed across numerous qubits for intricate calculations.
According to the Millisecond Coherence in a Superconducting Qubit publication released in June 2023, the longest coherence time of a qubit is 1.48 ms at an average gate fidelity of 99.991%. This percentage signifies the overall reliability of a QPU (quantum processing unit).
Currently, the most potent and functional quantum computer appears to be from IBM, referred to as Quantum System Two. A modular system geared for scaling, Quantum System Two is expected to execute 5,000 operations with three Heron QPUs in a single circuit by the close of 2024. By the end of 2033, this is anticipated to rise to 100 million operations.
The inquiry remains, would this sufficiently facilitate the realization of Shor’s algorithm and compromise Bitcoin?
QC Threat Viability
Due to decoherence complications and fault tolerance, quantum computers have yet to present a substantial threat to cryptography. It remains uncertain whether achieving a fault-tolerant quantum system at a large scale is feasible considering the required high level of environmental purity.
This encompasses electron-phonon scattering, photon emissions, and even electron-electron interactions. Furthermore, the greater the number of qubits needed for Shor’s algorithm, the more significant the decoherence.
Yet, while these might seem to be insurmountable issues intrinsic to quantum computing, notable advancements have been made in QEC strategies. A case in point, Riverlane’s Deltaflow 2 method executes real-time QEC on up to 250 qubits. By 2026, this technique is expected to culminate in the first functional quantum application with millions of real-time quantum operations (MegaQuOp).
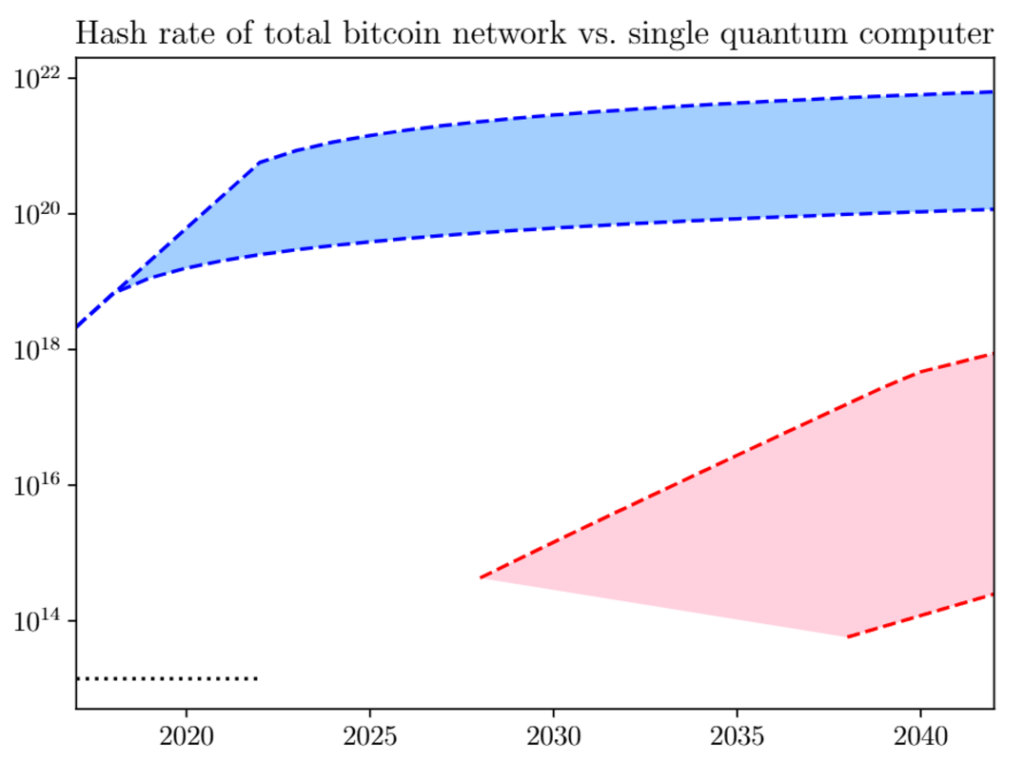
To compromise SHA-256 within a day, 13 million qubits would be necessary, according to the AVS Quantum Science article published in January 2022. While this would threaten Bitcoin wallets, a far larger number of qubits, around 1 billion, would be required to effectively conduct a 51% attack on Bitcoin’s mainnet.
Regarding the implementation of the Grover algorithm, designed to utilize QC to search through unstructured databases (unique hashes), a research paper published in 2018 indicated that no quantum computer would be capable of executing it before 2028.
Image credit: Ledger Journal
Naturally, the hashrate of the Bitcoin network has significantly escalated since then, and QC must contend with decoherence as a major hurdle. However, if QEC roadmaps ultimately evolve into reliable solutions, thenquantum systems, what measures can be implemented to mitigate the QC threat to Bitcoin?
Quantum Computing Fortification
Numerous recommendations exist to protect Bitcoin holders from quantum computers. Since a 51% QC assault is exceedingly unlikely, the primary emphasis is on reinforcing wallets. After all, if individuals cannot trust that their BTC assets are secure, it could trigger a mass exit from Bitcoin.
Consequently, the value of BTC would crash and the network’s hashrate would significantly diminish, rendering it much more susceptible to QC than previously anticipated. One of the fortifications is the adoption of Lamport signatures.
With Lamport signatures, a private key is created into pairs, producing 512 bitstrings from a 256-bit output. A public key is generated using a cryptographic function applied to each of the 512 bitstrings. Every BTC transaction would require a one-time Lamport signature.
Since Lamport signatures do not depend on elliptic curves over finite fields used in the Elliptic Curve Digital Signature Algorithm (ECDSA), which Bitcoin employs and is vulnerable to Shar’s algorithm, but rather on hash functions, this renders them a viable quantum-resistant alternative.
The drawback of Lamport signatures lies in their enlarged size, exceeding 16KB, and their single-use nature. Naturally, merely changing addresses and storing BTC in cold storage to avoid exposure of the private key can also hinder the effectiveness of QC.
Another strategy to thwart potential QC attacks would involve instituting lattice-based cryptography (LBC). Unlike ECDSA, LBC circumvents finite patterns by depending on discrete points in n-dimensional lattice (grid) space that extend indefinitely in all dimensions. Due to this characteristic, no quantum algorithm capable of breaking LBC has been devised yet.
Nevertheless, to implement a new form of cryptography, Bitcoin would need to execute a hard fork. In such a scenario, numerous indicators would likely be required to signal that significant advancements in quantum computing, particularly in qubit count and fault tolerance, are on the horizon.
Conclusion
It can be confidently stated that the Bitcoin mainnet itself is not at risk from quantum computing, whether in the near or distant future. Yet, should QC undermine Bitcoin’s encryption—rendering SHA-256 and ECDSA obsolete—it would severely influence confidence in the cryptocurrency.
This trust is vital, as evidenced by major corporations such as Microsoft and PayPal, which have embraced Bitcoin payments, attracted by savings of up to 80% compared to card transactions, zero chargebacks, and complete control over funds. With over 300 million holders worldwide, Bitcoin’s allure as both a secure asset and an economical payment option remains robust.
Ultimately, Bitcoin’s worth is underpinned by the capital and trust surrounding it. Its historical volatility illustrates how events—including Elon Musk’s tweets, PayPal’s integration, ETF launches, and the FTX collapse—have swayed market sentiment. A fundamental threat to Bitcoin’s encryption could incite frantic sell-offs, miner exits, and lowered mining difficulty, potentially paving the way for a 51% QC attack with fewer qubits.
To avert such an outcome, Bitcoin holders and developers would benefit from staying updated on QC advancements.
This is a guest article by Shane Neagle. The viewpoints expressed are solely his own and do not necessarily mirror those of BTC Inc or Bitcoin Magazine.